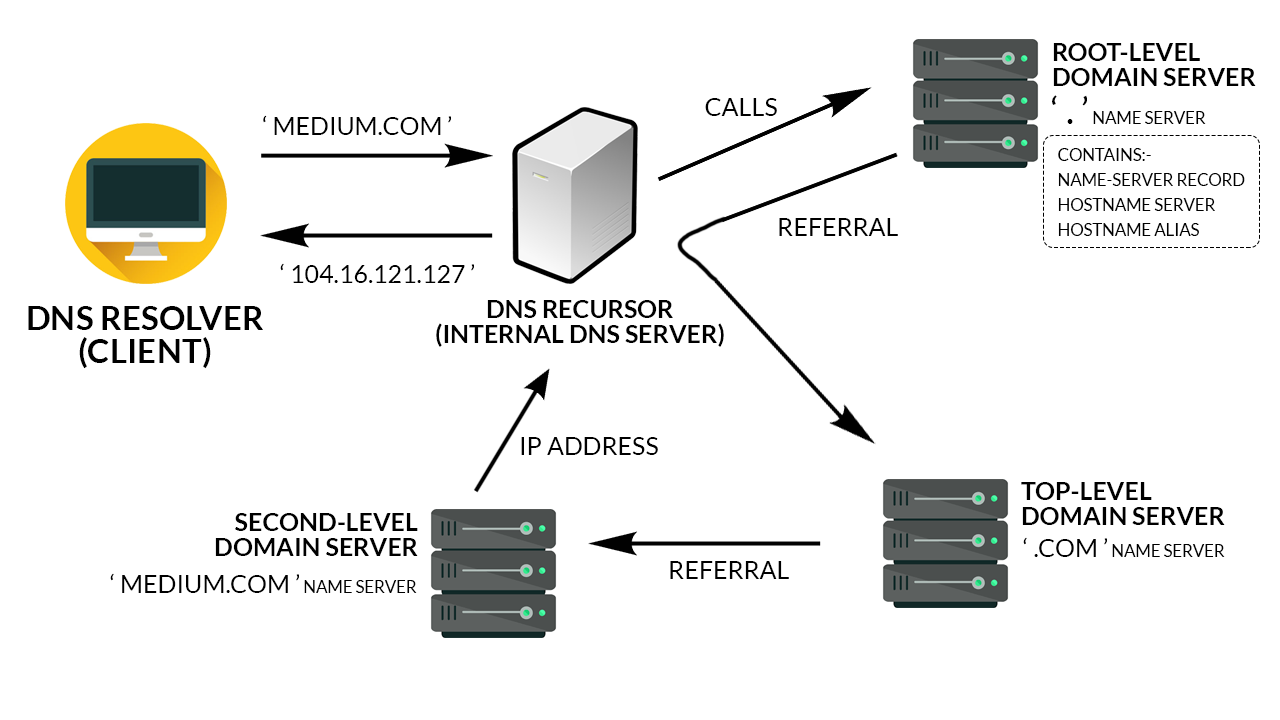
Social Media Image Sizes
Complete guide to social media image sizes for 2025. Get the exact dimensions for Facebook, Twitter, Instagram, LinkedIn, and more. Includes profile pictures, cover photos, shared images, and advertising specs to optimize your social media presence.